MANIFEST
The evolution of cybernetization
Science ⬇ Engineering ⬇ Business ⬇ Social media ⬇ Money ⬇ Power
The continuous encroachment and integration of cybernetics, or the ‘cybernetization’ of human civilization, takes its roots with the gradual evolution of mathematical concepts and ideas building from it. Generations of human engineers continued the development of the exact science, eventually implementing the extruded ideas in computing and ‘thinking’ machines. The latter started being disseminated freely among enthusiasts, who, in turn, attempted to apply them in business applications. With the involvement of the ever-expanding strata of the population, social networks came into prominence. The emergence of Bitcoin as the first digital means of transaction, one independent of the traditional economic system, marked the beginning of the cybernetization in the financial sector. But more important than that aspect, Bitcoin proved it to be fundamentally feasible to create and successfully operate consensus protocols, making it, in turn, possible to establish fully distributed cybernetic communities resistant to any form of external influence, ones that would be controlled exclusively by the rules they themselves set. The last remaining sector that the phenomenon of cybernetization should evolutionarily penetrate is the process of governance of society – the framework of power and underlying politics.
It is vital to underscore the fact that Bitcoin is primarily a social phenomenon and its advantages are largely social, extending to its invulnerability to external influence, its reliability, deflationary dynamics, and others. At the same time, in terms of functions of electronic money, it did not introduce any fundamental innovations. In particular, WebMoney, developed earlier, also performed all the customary functions of electronic money, however, due to its centralized design, WebMoney was vulnerable to all manner of threats, and it did not give its holders any distinct advantages compared to a regular bank card or account, preventing it from taking up the mantel of a revolutionary means of transaction. Being inherently decentralized, Bitcoin is not prone to these risks. On the other hand, practical experience has proven that blockchain solutions are ill-suited for businesses settings. The main reason for that is because the blockchain is far worse than conventional centralized solutions in terms of efficiency and cannot improve business processes. Blockchain technology was originally designed to solve entirely different problems – a clause explicitly outlined in the Bitcoin white paper, and one applicable to all other decentralized protocols.
Taking into account the aforementioned factors, it is necessary to understand and accept that the mission of blockchain technologies resides in the social spectrum and in the political arena in the long term. At the same time, the unique properties that consensus protocols are endowed with open up the possibility of creating new social structures that were previously impossible to conceive. These structures, existing exclusively in cyberspace, are nevertheless capable of being resistant to the influence of the established system of power, and can therefore operate, develop, and be governed based on their own rules. Moreover, due to their decentralized nature, governance in these systems is transparent and egalitarian, and free from corruption in one form or another due to the exclusion of the human factor at the level of submission to the accepted rules. This is achieved thanks to two important characteristic of consensus databases. The first one is liveness. Bitcoin has proven that it is possible to create a system that can exist without being subject to any external regulatory influence. The second is inevitability of execution. If an action has been initiated and does not violate the rules of consensus, then the efforts required to stop its execution is equal to the effort needed to disrupt the network itself — which, given the first characteristic, makes such a scenario practically impossible.
Cybernetic Community Platforms
(CCP)
Cyber – Existing in cyberspace.
Community – A community of people, devices or AI with common interests.
Platform – An infrastructure and accompanying software that provides a reliable and secure environment for interaction.
- Peer-to-peer or centralized (less secure).
- Open database using consensus protocols.
- General purpose logic or specialized logic.
- Transparent governance by the community, AI, or a hybrid combination of both.
- Decision-making based on a referendum or representation basis.
- Community-defined values.
- Resistance to censorship.
- Freedom from government and corporate control.
- Unbiased media.
- Digitalization without the creation of ‘digital concentration camp’.
- Increase in the connectivity of the world without the distortion of traditional media.
- Cybernetic constructs as prototypes of future political systems based in the real world.
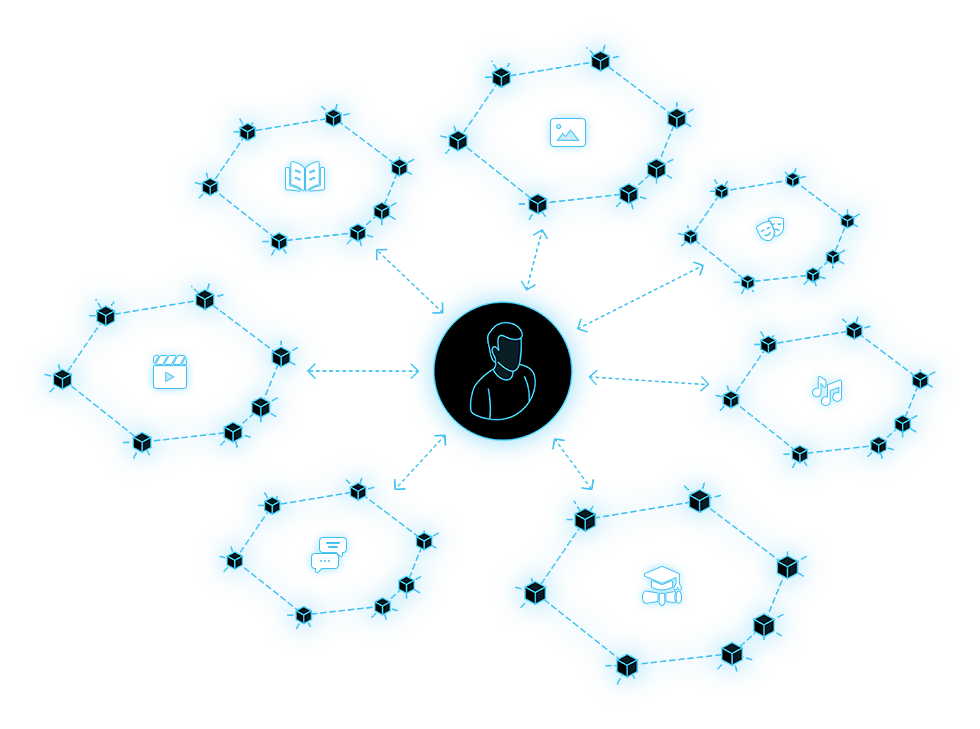
The Cybernetic Community Platform is a high-trust environment in cyberspace that allows people, devices, or AI to interact based on a common interest. Such platforms are mainly peer-to-peer networks with an open distributed database based on a consensus protocol. However, the system can also be implemented as a centralized solution, although the degree of trust within the scope of such a platform will always be much lower than in a decentralized one due to reduced degree of resistance to censorship and other threats. Such a community has complete freedom to determine its own values and rules of existence. Direct management of the rules can be formalized on the basis of a classic voting mechanism or through the transfer of this function to transparently trained AI, or a hybrid of both methods.
Vision of the Future Internet
Network of Cybernetic Community PlatformsThe obvious advantages of such networks over traditional platforms with centralized management and ownership will gradually result in the ousting of the latter from socially significant sectors of information services provision, and new ones will be created on this basis. As the number of such structures grows, their dominance on the Internet will become overwhelming, and the paradigm of transparency, fairness and egalitarianism that they bring will become the norm of social organization in cyberspace.
States and corporations strive to gain total control over people’s consciousness and ultimately establish a so-called ‘digital concentration camp’. A cybernetic society consisting of various self-regulating communities puts forward an approach to the digitalization of society without the formation of a ‘digital concentration camp’ through the involvement of people in decision-making, offering complete transparency and the inevitability of their implementation in the original form in which they were accepted by the community.
These principles make it possible to create unbiased autonomous media by eliminating the influence of one or a few subjects on editorial policy. They also allow the formation of a most objective view of the world among the planet’s population through the elimination of bias and prejudice, which, in turn, leads to a more adequate worldview and the improvement of life in general.
As the influence of such a cybernetic society grows, its governance practices will inevitably spill over into the real world, offering an alternative to traditional state and international institutions with all their millennia-old unresolved vices. Resistance to these trends will always be considered by supporters of open and transparent cyber-based communities as a futile effort to protect the corruption and depravity of old political systems.
Cybernetic Communities Common Protocol
(CCCP)
- Protocol for interaction between CCPs.
- Peer-to-peer topology (P2P).
- Provision of information about shared assets, such as accounts.
- Provision of data and methods (client software) for reaching subsidiary networks.
- Provision of means for tokenized assets and messages to move between platforms.
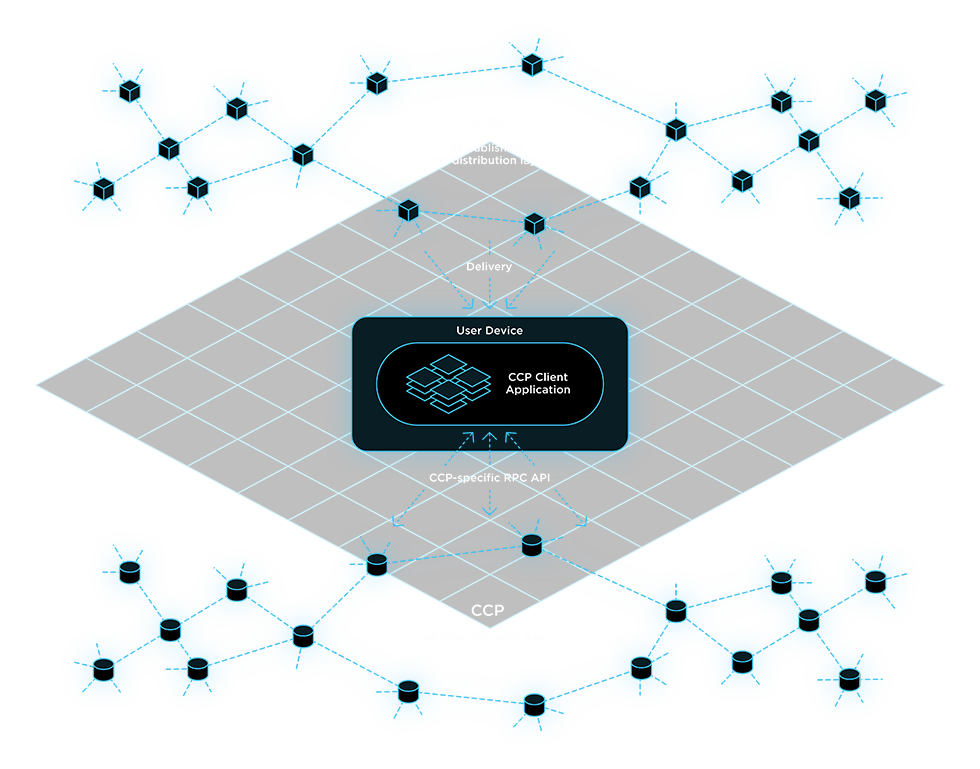
The Cybernetic Communities Common Protocol is a universal protocol that provides for the exchange of values and messages between CCPs as independent communication units, and allows for the receipt of network-specific information about common assets, such as account information. The transmitted value can be expressed in the form of tokens and tokenized assets of the networks themselves. The concept of the message transmitted from one network to another is still a subject for further research
Subsidiary Networks
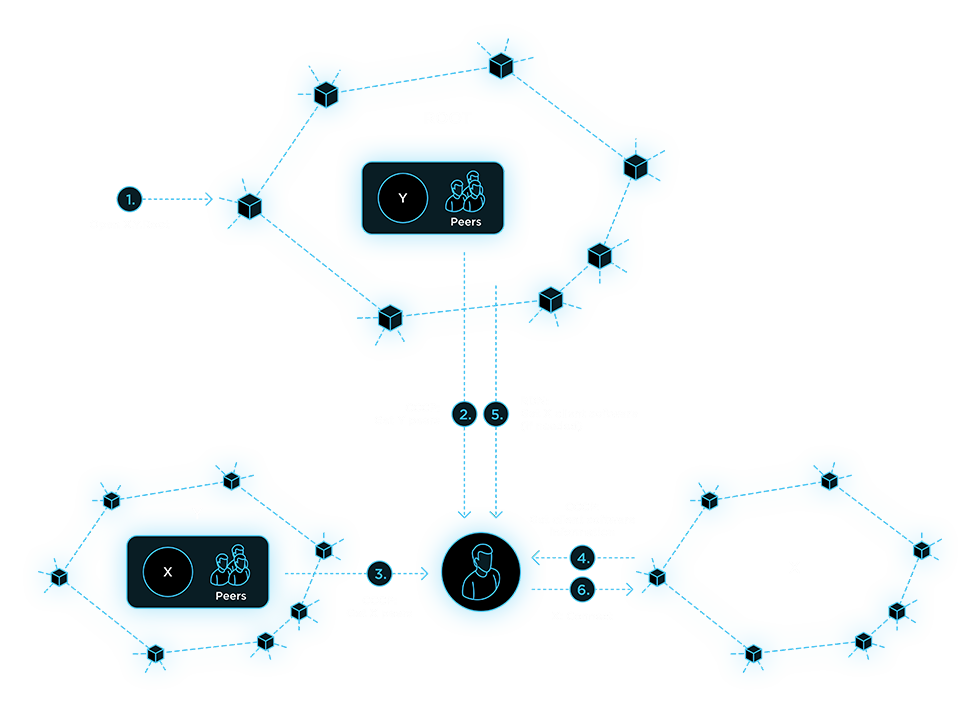
Any CCP can register itself in any other network as a child and exchange data with it via the CCCP protocol. This also allows entities to find a network by its full address, which is the path from one network to another. Registration implies receiving a name that is unique within the network. The RDN always acts as the root network. This means that if any entity needs to access the zyx network, the first step implies “x” being searched among registered RDN networks, then “y” among networks registered in “x”, and finally “z” among networks registered in “y”. If necessary, the CCCP protocol also allows entities to request information from a specified network about the client software required to interact with it.
Universal Cryptographic User Account
- One account for authorization on many platforms.
- Ability to have multiple accounts.
- Digital identity based on free will.
The Universal Cryptographic User Account is a universal set of rules defining user authentication in CCPs that support this feature. It represents a simple public/private key pair for the digital signature algorithm and allows users to log into the CCP without going through the traditional registration procedure. A single account can be used in different networks.
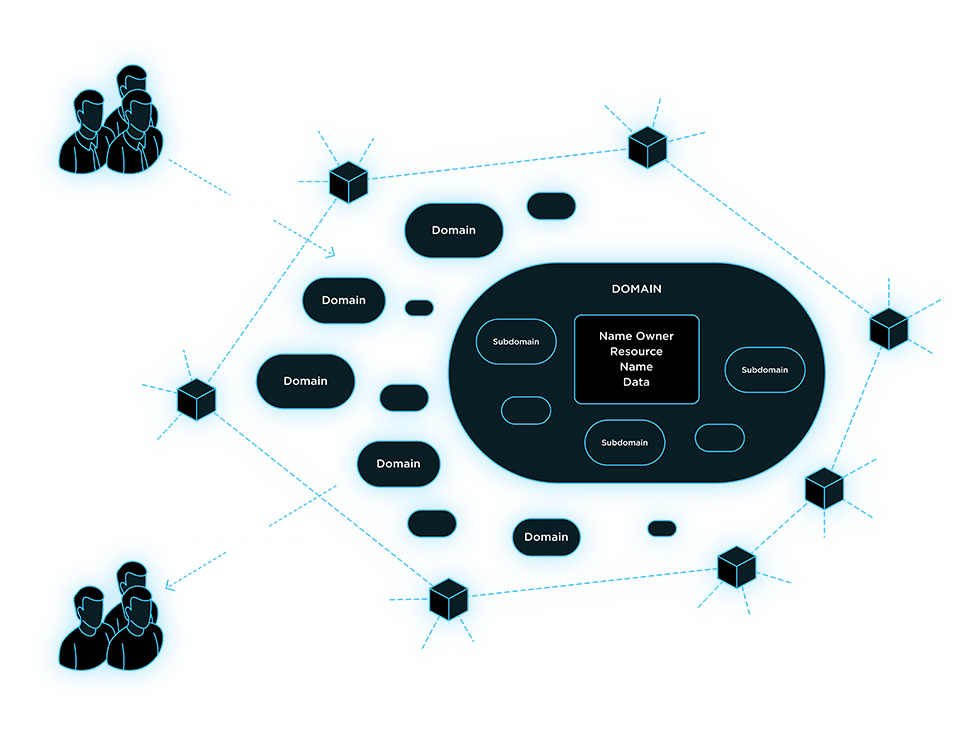
Resource Distribution Network - Root CCP
(RDN)
- Decentralized dereferencing (analogous to a DNS).
- Decentralized publishing and distribution of data and content of any kind.
- P2P file sharing.
- Infrastructure layer to replace traditional web stack with universal platform-independent applications.
- Anti-malware protocol.
- Meta resources, such as software packages.
- Reverse Search.
The Resource Distribution Network is designed to publish various resources for download and distribution by other users. It is an open P2P network consisting of a distributed database based on MCV consensus protocol and a file-sharing network. Within the terminology of this network, a resource is any static data block, file or files (content).
A domain is a unit of ownership of resources in the RDN, functionally similar to a web domain. A domain has a unique global name, which comes in 3 types: free, migrated, and national. Free ones begin with “_” and can be registered by anyone. Migrated ones begin with a letter or number and are registered by proving priority ownership of a web domain with the same name. National ones end with “ * ” and are intended for states and larger public associations.
A resource consists of a name and an arbitrary block of data of limited length. The full address of a resource consists of the domain name and the resource name. If a resource is a file or files, then its associated data is the hash address of its file or files. In this case, the content itself is published in a P2P file-sharing network, which is part of the RDN.
A special case of a resource consists of packages. Packages are primarily intended for publishing software distributions, but can be used for any other types of content. This feature opens up the possibility to create the first single universal decentralized package database in the history of the Internet.
The RDN allows for the implementation of the so-called “reverse search”. It is the ability of the publisher to place some data supplemented with special meta information describing its type. Then, by monitoring the network, all agents interested in data of this type can find it using meta information, check it for adequacy and relevancy, and use it in one way or another for their own purposes.
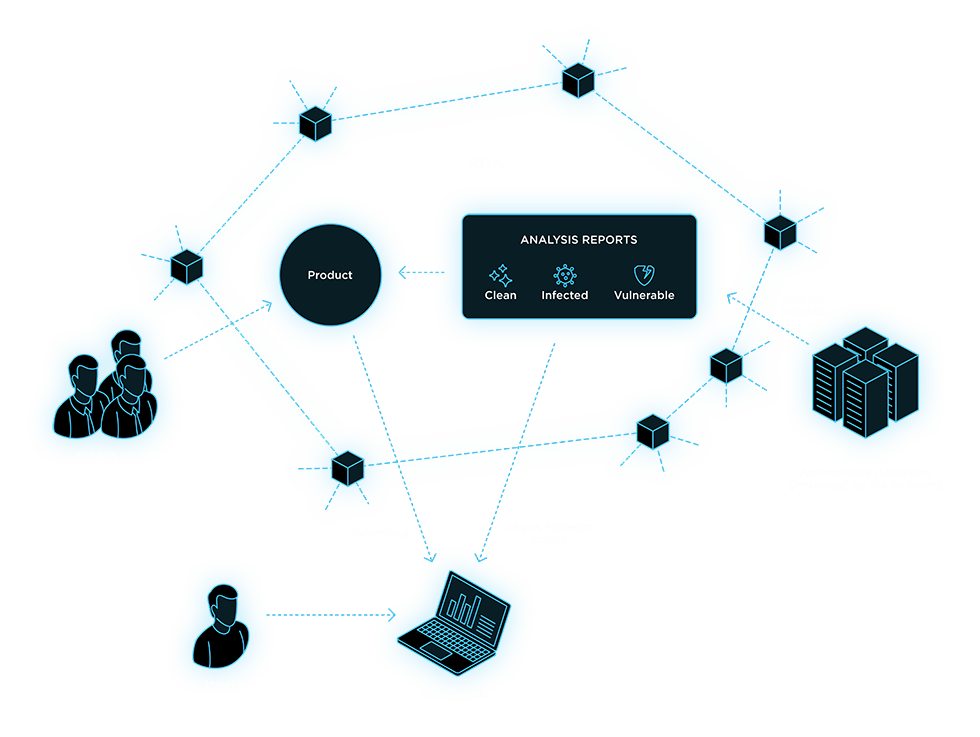
Anti-malware Protection Protocol
(AMPP)
- The RDN allows publishers to request their content to be analyzed for malware.
- Received approvals increase the trust in the published software.
- Eliminates the need for local antivirus software, avoiding associated performance degradation.
- Use of a specialized malware analyzer infrastructure allows for much deeper (AI-based) and more comprehensive and heuristic analysis of software binaries.
The Antimalware Protection Protocol (AMPP) is a protocol and set of special functions that serve to minimize malicious activity that may be caused by software distributed through the RDN. Its main purpose is to independently check application releases by trusted agents for malware and publish reports to all users.
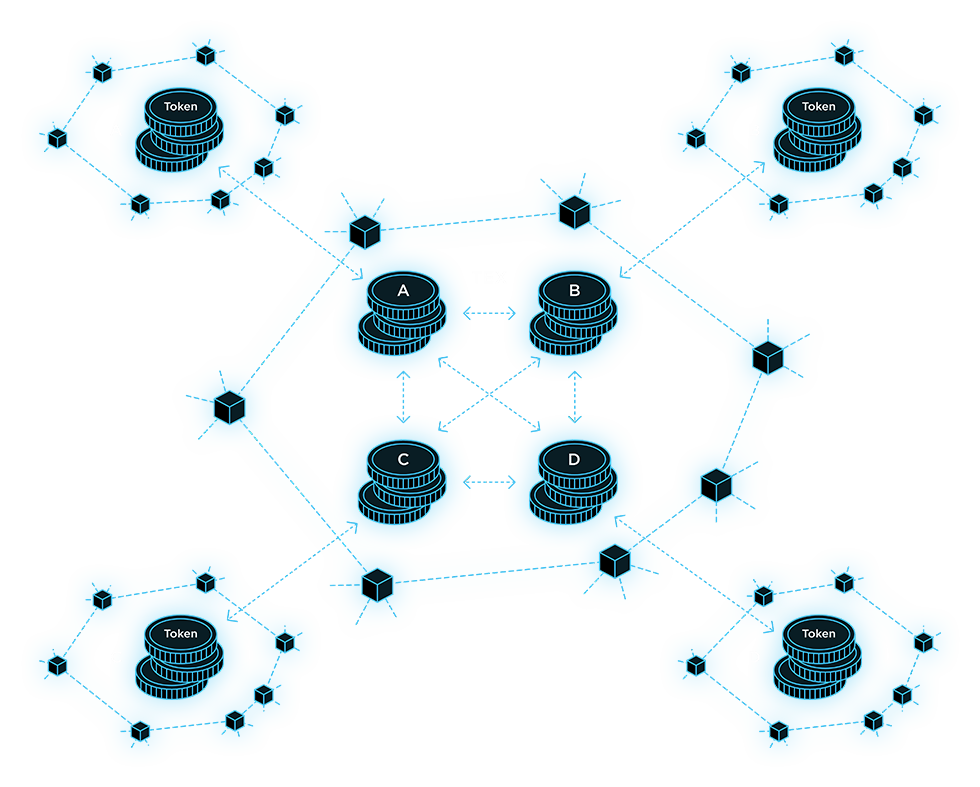
Token Exchange CCP
(TEX)
- Exchange any CCP token for any other token.
- The input/output of tokens from TEX and reverse action is one of the functions of the CCCP protocol.
- Works seamlessly for the user, so they can use a token from one CCP for the purposes of another CCP.
Each CCP can issue one or more tokens. Multiple networks imply the issuance of multiple tokens – a factor that can result in considerable inconvenience to users. To solve this problem, the CCP Token Exchange (TEX) will act as a decentralized exchange service. Other networks can register in this network and introduce their tokens into it via the CCCP protocol. This service allows regular users to spend one token for payments in other networks through an implicit automatic exchange of one token for another.
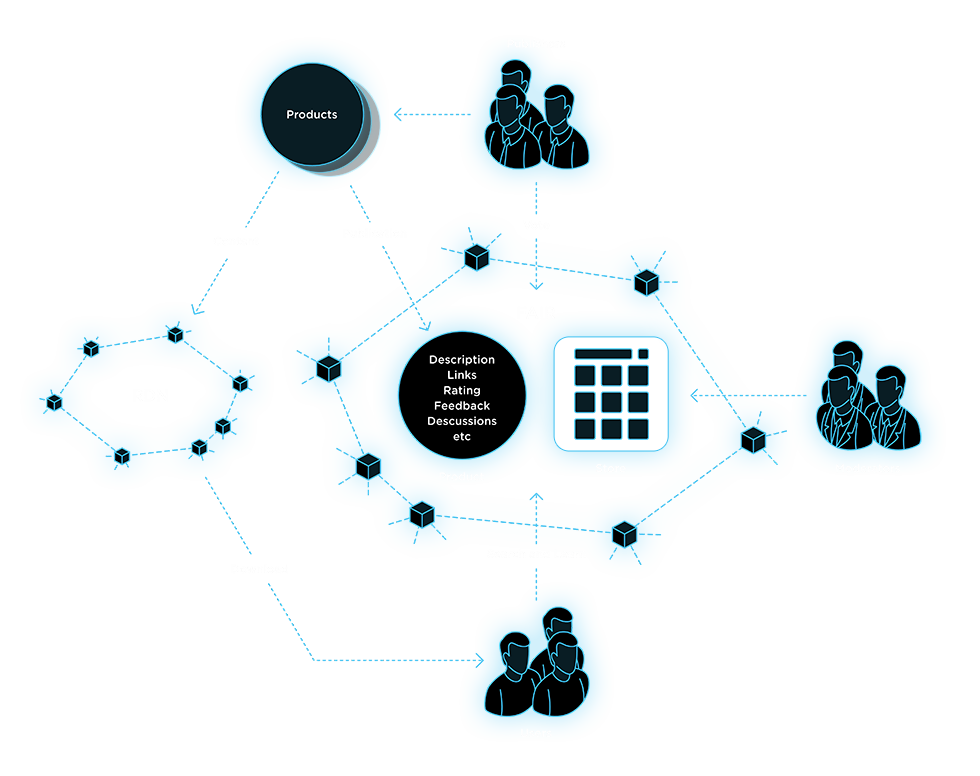
The Fair CCP
- Social network of Stores.
- Each store is similar to App Store / PlayMarket / Steam / Torrent Tracker etc.
- Product publishing.
- Search for products.
- Download from the RDN or via any other provider.
- Provide feedback.
- Publishers have priority in decision-making through voting.
- Elected moderators keep content clean and relevant.
The Fair is a decentralized platform for creating autonomous, self-governing store-like sites. Each such site allows users to publish and moderate information about various digital products.
A product can be anything that can be downloaded from the Internet. The product base is formed by publishers. A publisher can be anyone who offers a product or products.
A store can be created by anyone willing. That user can then include other members (publishers or authors), who receive the same rights as the founder. Publishers can elect moderators, who constantly monitor the observance of the rules by other users and publishers themselves. A referendum among all members always maintains the highest priority and can cancel or alter any decisions, particularly the ones that are made by moderators. The values and rules of each store are laid by the respective community. Stores compete with each other by offering the best moderation policy and content management. Other users can participate in the formation of ratings, reviews, and other social activities.